Announcing Kubernetes Fury Auth
The new KFD Core Module for Authentication and Authorization Management
Version 1.24 of our Kubernetes Fury Distribution (KFD) came with the announcement of many new features and updates. In our previous blog post, we guided you through some of the highlights of this new release, such as introducing guide paths with release upgrades, significantly refactoring the logging module, and more.
Today, we’re happy to introduce you to our new core module: Kubernetes Fury Auth.
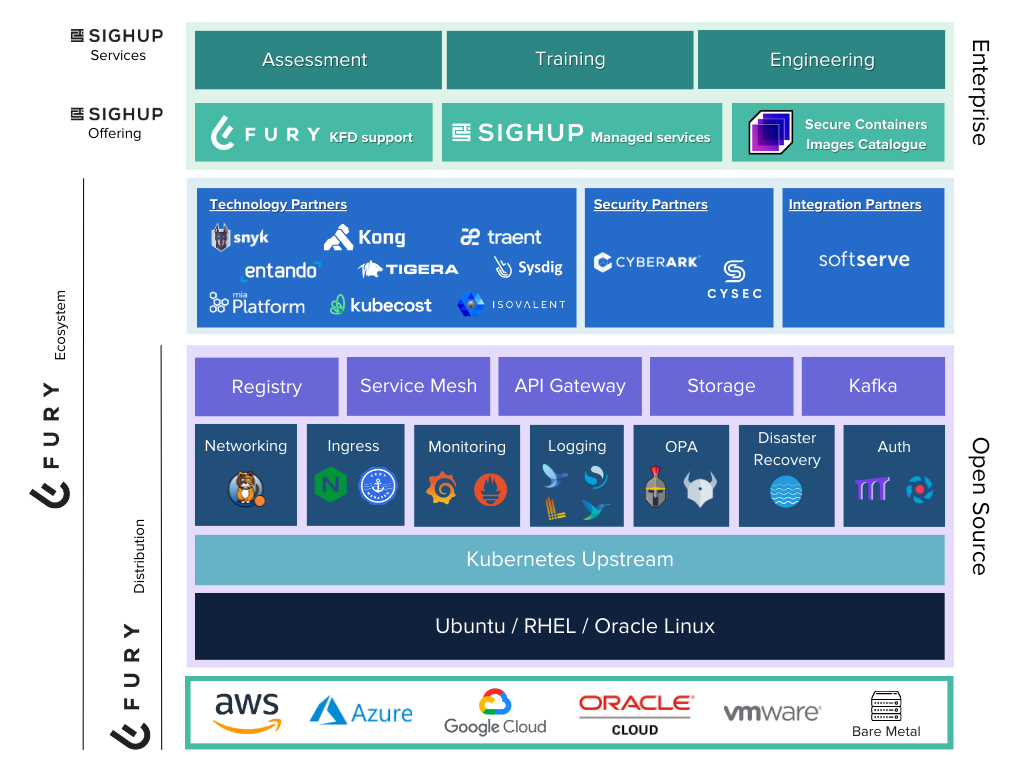
Overview of Kubernetes Fury Auth
Kubernetes Fury Auth provides Authentication and Authorization Management for Kubernetes Fury Distribution (KFD).
An ingress is the mechanism by which Kubernetes exposes applications outside the cluster.
A KFD user who has deployed ("installed") its application into a cluster, in order for people to access it, must create an ingress that exposes the application.
The exposed application could not have the ability to protect access to itself, for example, by asking username & password before giving access.
The Auth module solves this problem, ensuring that when someone wants to access the applications, they must first authenticate. It also allows you to connect these tools to the user identity management system (Identity Provider). Once authenticated, the Auth module can also enforce authorization on the user. For example, the user must be a member of a user group to access.
Although this set of tools was already in our distribution, spread across various modules (especially the Ingress module), over time, we noticed that it could’ve been hard to find all the configurations needed.
This new module doesn’t introduce new tools in KFD but moves all the authentication and authorization packages to this new core module.
We decided to group them into a dedicated module to provide a better developer experience.
Now we give proper visibility to all the authorization tools and to the goals they pursue, returning to users an architecture more orderly, with greater ease of use, and optimization of ingresses security.
In addition, users can now easily access the tools, in case they have the right, to disable the functionality of the Auth module, operating selectively compared to the ingress of the single application.
Kubernetes Fury Auth uses the following CNCF-recommended Cloud Native packages and consists of these three tools: Pomerium, Dex, and Gangway.
These are all CNCF-Certified Open Source tools, as for all the other tools in our distribution.
They respond to the following needs:
- Pomerium enables secure access to applications by providing a standardized interface, regardless of whether the application itself has authorization or authentication baked-in;
- Dex is an identity service that uses OpenID Connect (OIDC) to drive authentication for exposed apps;
- Gangway allows users to self-configure authentication flows using OIDC Tokens to identify users who access a Kubernetes cluster.
Conclusions
The introduction of the new Core Module Kubernetes Fury Auth reflects our continuous efforts to expand and maintain the Kubernetes Fury ecosystem to keep up with the latest upstream changes while keeping our distribution constantly up-to-date, simple to use, and secure.
This new core module aims to give more visibility to all the Authentication and Authorization tools in our Kubernetes Distribution returning to users an architecture more orderly, with greater ease of use, and optimization of ingresses security.
The news around our major release of KFD doesn’t end up here: we can’t wait to let you know more about our new Add-on Modules!

