Easily manage OPA Gatekeeper rules with Gatekeeper Policy Manager
A simple to use, open-source, web-based tool to see the OPA Gatekeeper's policies deployed in your cluster and their status.

We're pleased to announce the first release of Gatekeeper Policy Manager (GPM), a simple to use, open-source, web-based tool to see the OPA Gatekeeper's policies deployed in your cluster, and their status.
You might be familiar with the OPA Gatekeeper project. This project lets you define policies as code using the Rego language and enforces them in your Kubernetes cluster using Open Policy Agent. OPA Gatekeeper leverages the creation of custom Kubernetes resources definition (CRD) objects, such as "Constraint Templates" or "Constraints", containing and enforcing Policies with the Rego language.
While this pattern is compelling, not everyone is comfortable using CLI/Yaml to inspect Rego code, policies, and violations. This is why we developed GPM: we wanted to provide an easy (yet powerful) way to inspect all Constraints definitions for your cluster.
With GPM you'll be able to check Constraints definitions, Rego code, and related statuses - both for running and rules defined in dry-run mode.
We hope you will enjoy the Gatekeeper Policies Manager. If you have any feedback or suggestions, feel free to open an Issue or a PR.
Want to check it out? You can find the project on Github and a few screenshots below.
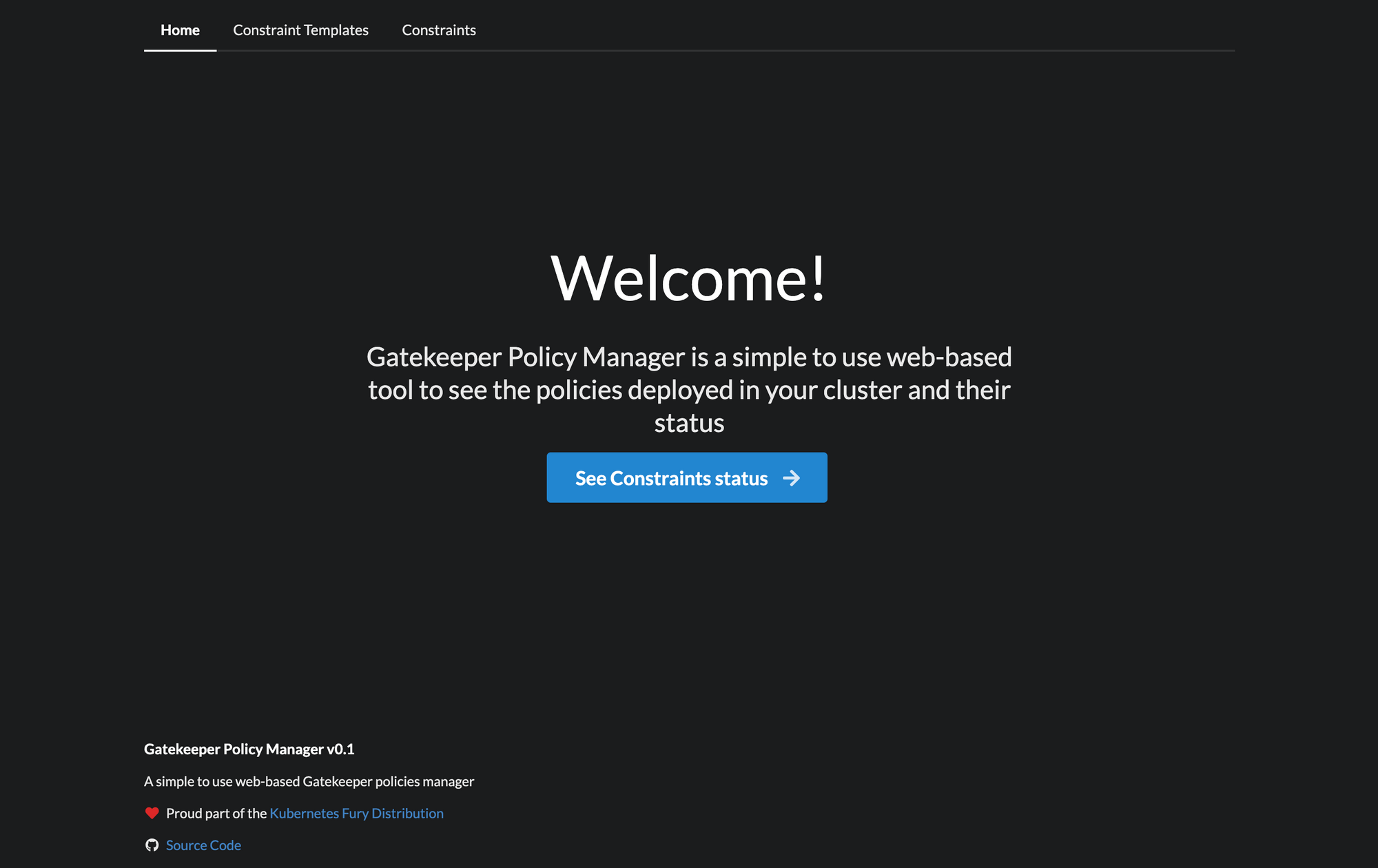
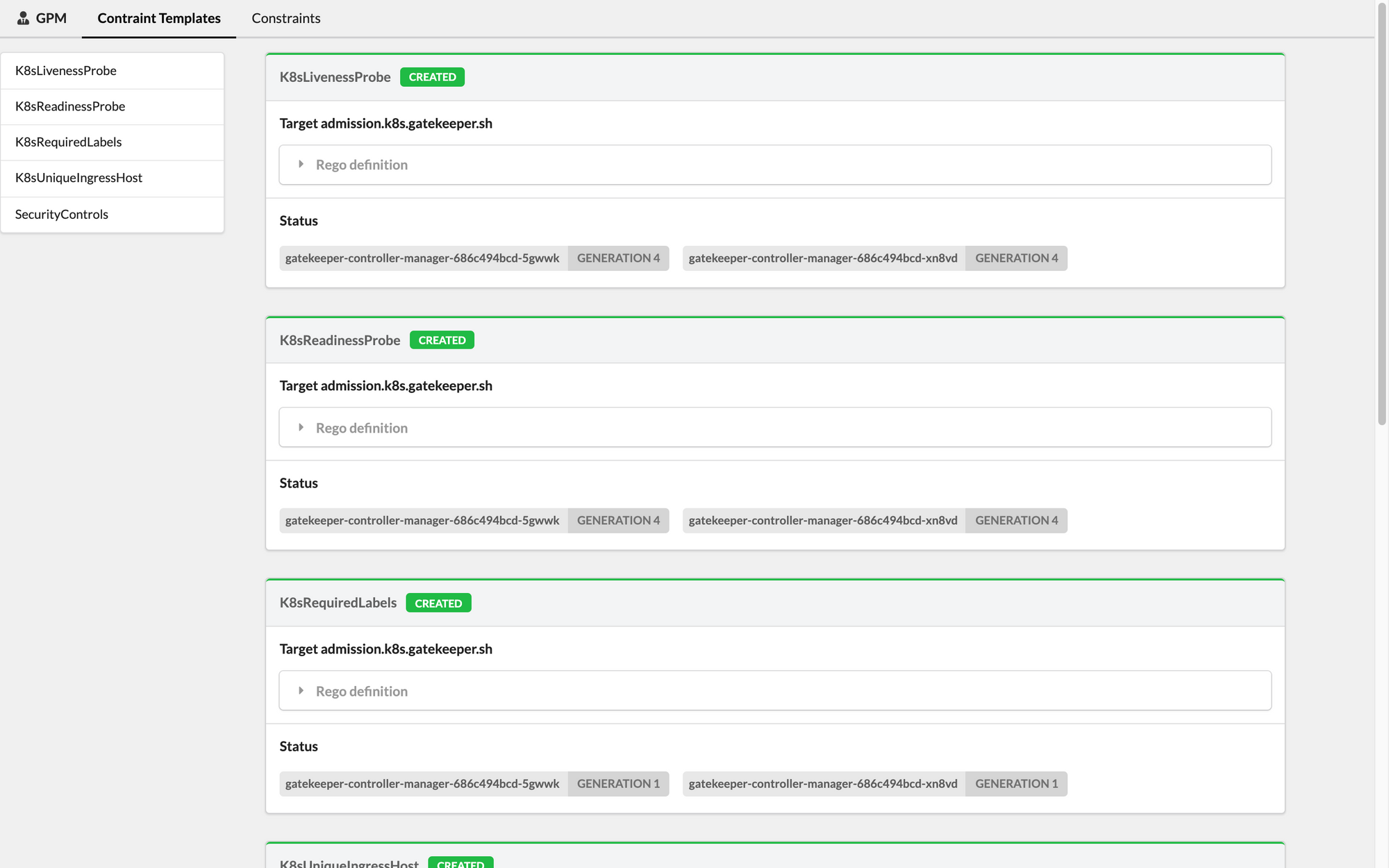
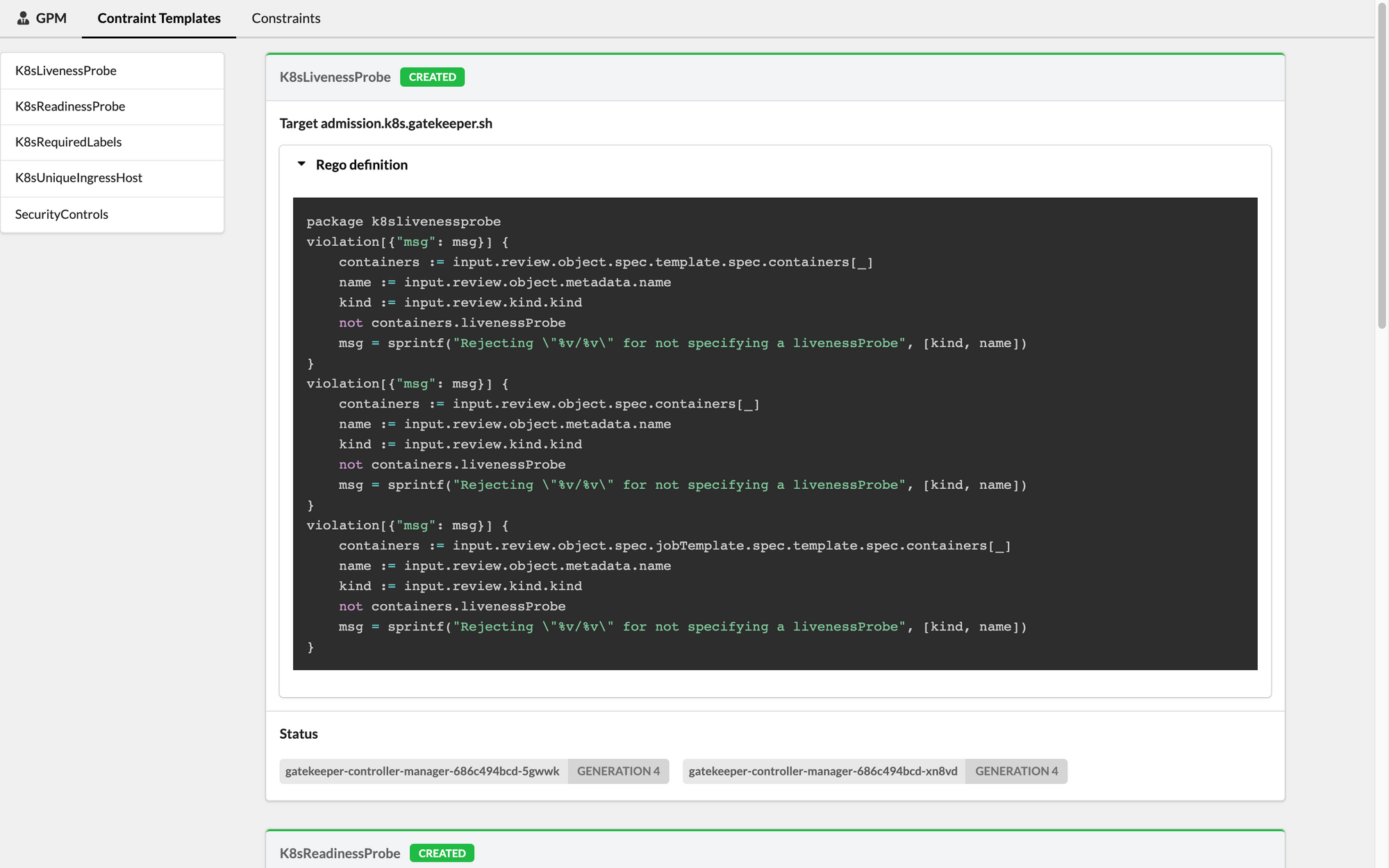
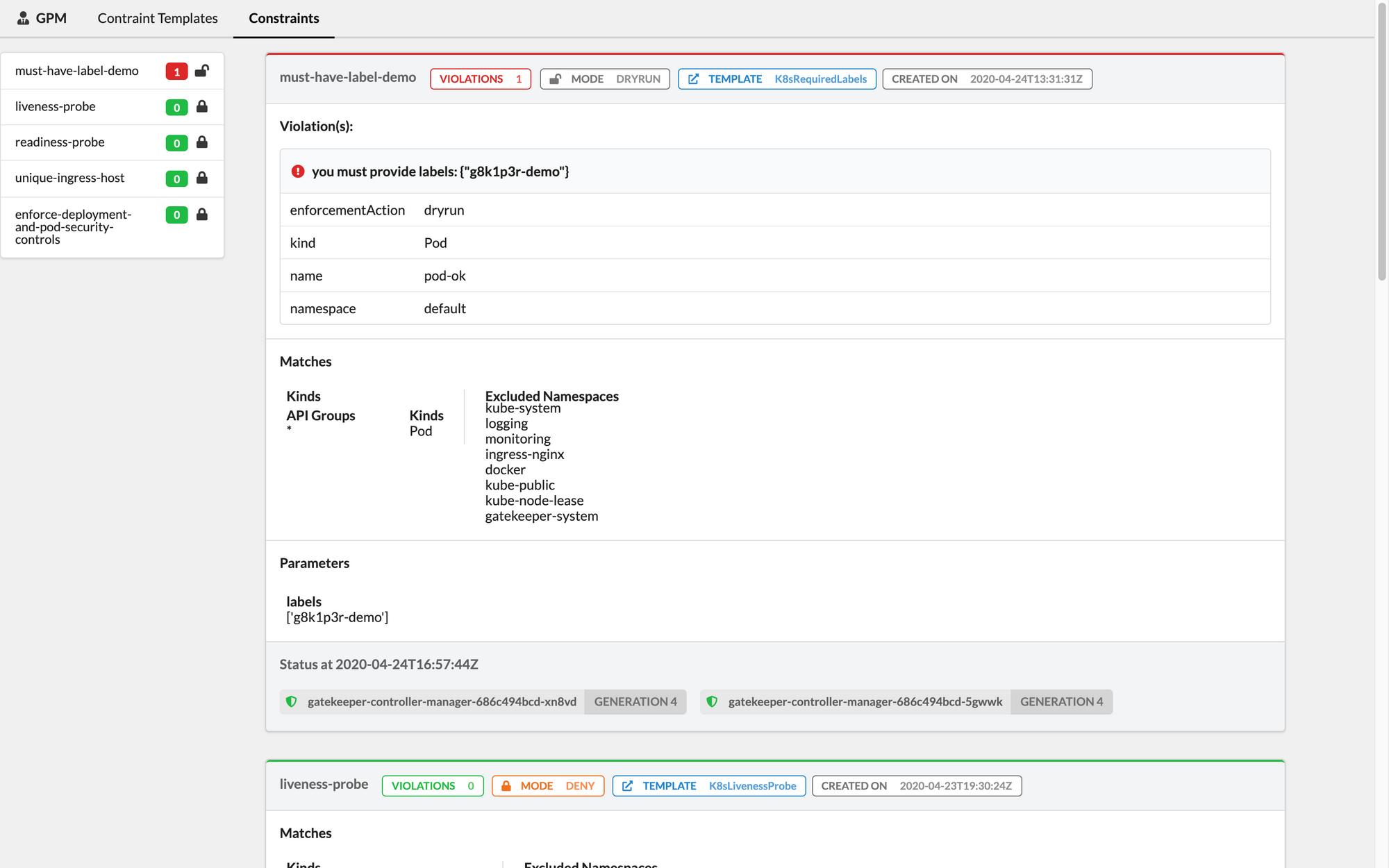
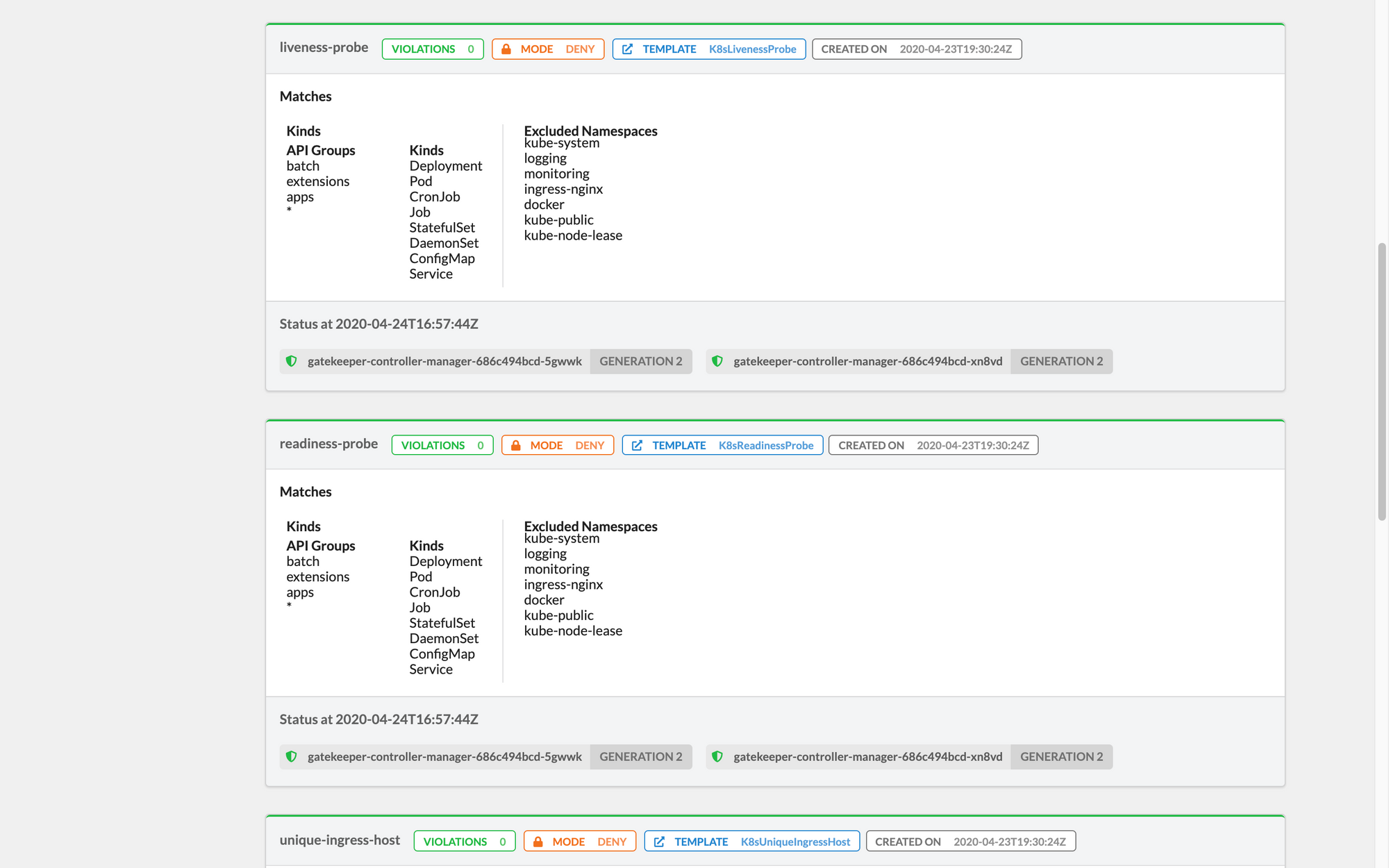
If you haven't tried OPA Gatekeeper yet, we also invite you to try out our Fury Kubernetes OPA module and our CNCF certified and battle-tested Kubernetes Fury Distribution.
