Announcing our latest release of Kubernetes Fury Distribution (KFD) - Fury v1.1

We are happy to announce our amazing Product Team at SIGHUP has just released v1.1 for Kubernetes Fury Distribution. This update comes with a ton of changes - you can check out the official release page on GitHub, linked above, but here are the highlights of our biggest core changes.

Addition of the OPA module
We don't take production-readiness for granted. We make it happen. KFD v1.1 adds the possibility to decrease attack vectors, and increase resilience and stability as simple as activating the OPA module. The Gatekeeper project uses the Open Policy Agent to deny or allow deployments based on some simple rules.
Using the Admission Controller Webhooks, the Gatekeeper intercepts an API request to apply the defined rules.
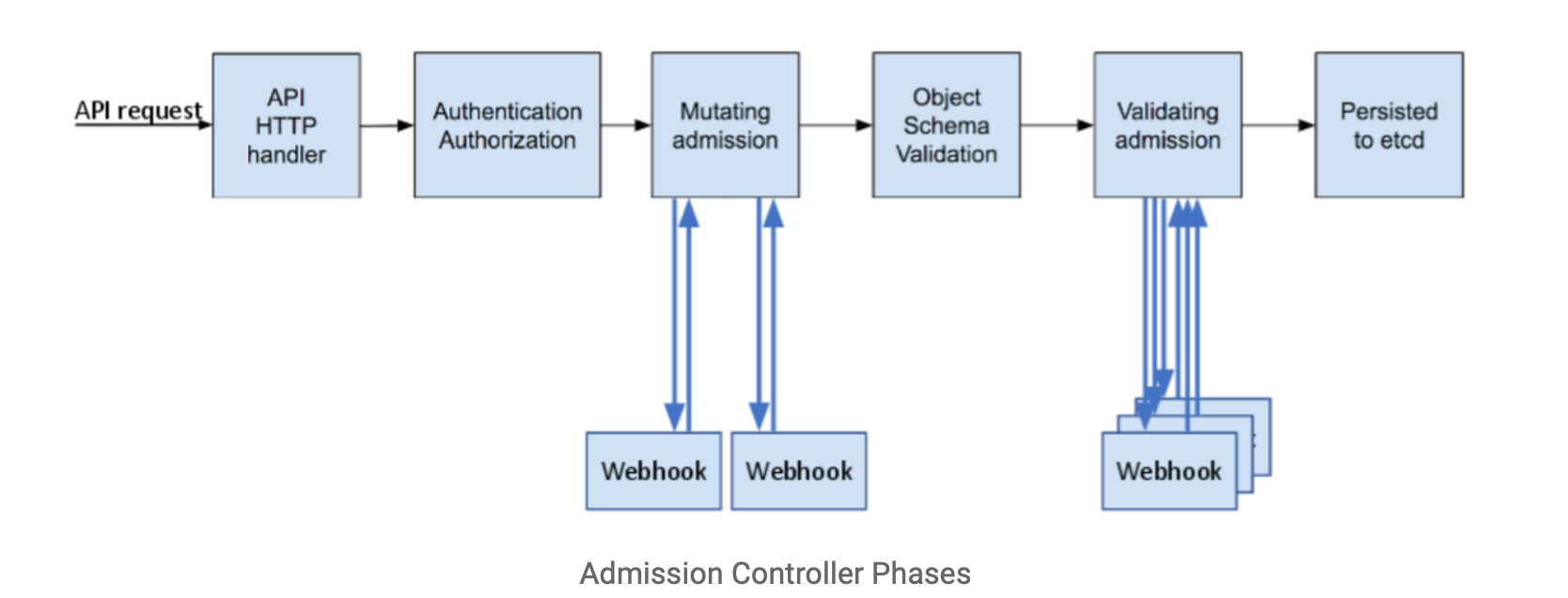
The OPA module has some useful pre-defined rules for Gatekeeper like:
- denial of docker images with
latesttag - denial of pods that have no limit declared (both CPU and Memory)
- denial of pods that explicitly allow privilege escalation
- denial of pods that run as root
- denial of pods that do not declare
livenessProbeandreadinessProbe - denial of duplicated ingresses
Network shaping
From the previous version of KFD, we've not only kept the commitment to be compatible with 3 consecutive Kubernetes versions, we've also made a step further in reliability, providing a straightforward way to limit the network budget of the pods. We limit the bandwidth each pod can consume, to ensure the reliability of the services in the cluster.

So you can add the kubernetes.io/ingress-bandwidth and kubernetes.io/egress-bandwidth annotations to your pod as follows:
apiVersion: v1
kind: Pod
metadata:
annotations:
kubernetes.io/ingress-bandwidth: 1M
kubernetes.io/egress-bandwidth: 1M
...
Cert-manager
If we can agree on something about Kubernetes maintenance, it's that certificates rotation is not something easy nor pleasant to do manually. But you know, if it's hard -> do it daily, if it's a nightmare -> automate it so we rely heavily on Jetstack cert-manager to fully automate the certificates lifecycle.

Smooth operations
Moving into the cluster with minimum waste and maximum joy is crucial in our battle-tested Fury Distribution. For v1.1 we added some interesting features, like ensuring that kubectl top {pod,node} works in all the supported Kubernetes versions, so inspectability is on point.

Also, reproducibility is increased with automated detection for some common pitfalls, like re-using the machine-id, which is a common bug with AMIs or pre-built on-premise images. We've got you covered by introducing a set of alerts for this scenario.
Finally we do a huge third party for our networking, monitoring, ingress and disaster recovery core modules.
Communication is key - announcing our Documentation Portal
If a tree falls in a forest and no one is around to hear it, does it make a sound? Sure it does (we know science), but surely it won't have any impact. This is why we are happy to announce the Kubernetes Fury Documentation Portal with insights and useful tutorials for KFD v1.1. And this is just the beginning.

📦 Wrapping it up
You can find the complete changelog here, and you can find us at sighup.io creating other battle-tested awesome products like this one. You can check out the CNCF landscape, for example.

