Secrets manager? Yes please! Some insight about CyberArk Conjur
In the last years, an explosion of human and not human identities has changed our corporations. Cloud workloads need to be identified and granted in the correct way. CyberArk Conjur, together SIGHUP expertise can solve these needs in the right way.

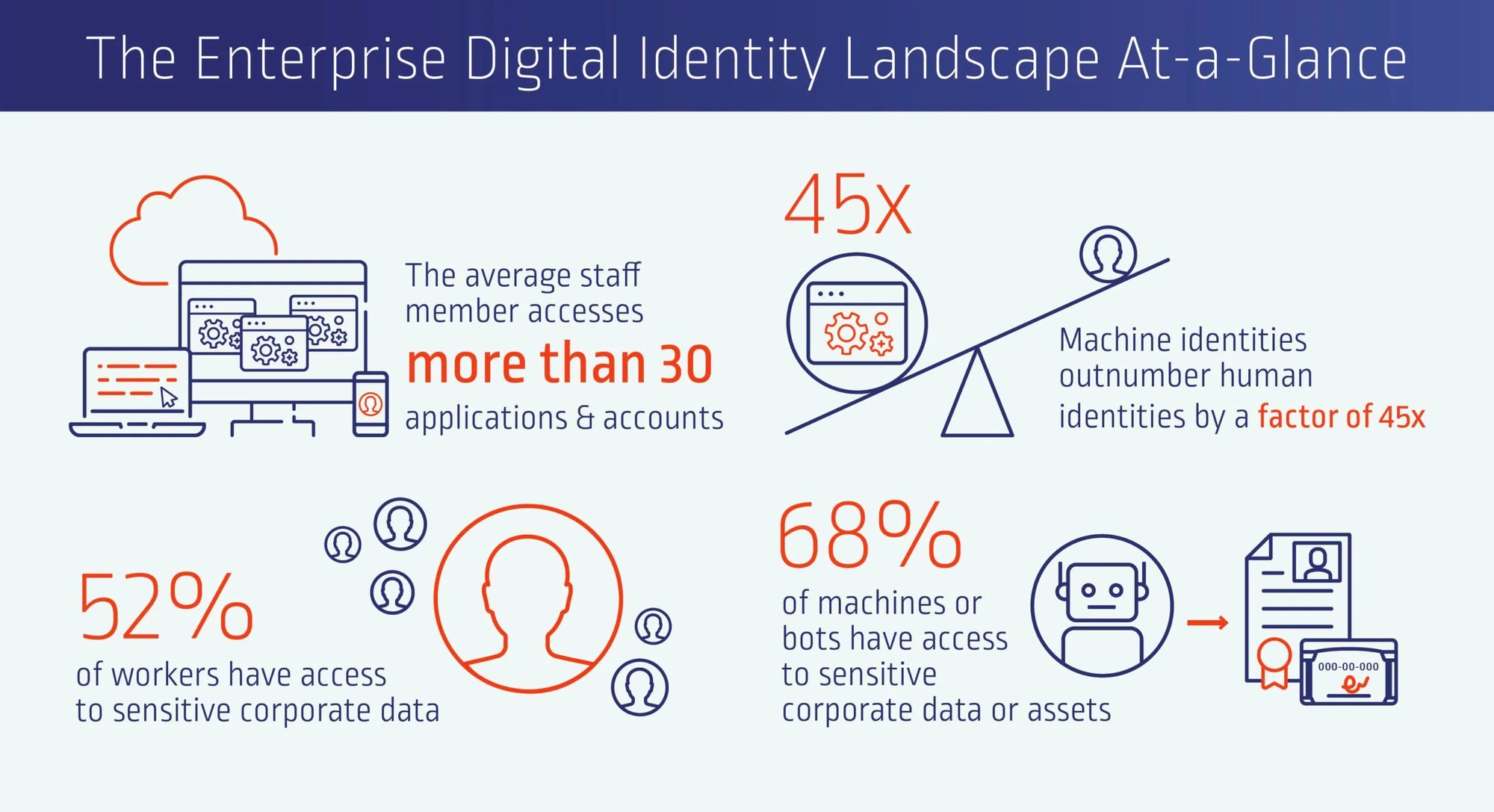
We cannot talk about a secrets manager without a little introduction about identities. In the last years, digital transformations and the cloud journey caused a massive growth of Identities.
As you can see in this image from a CyberArk article, the number of accounts exploded, and a lot of human and non-human accounts have the right to access sensitive data.
Another critical point is how to recognize the cloud workloads:
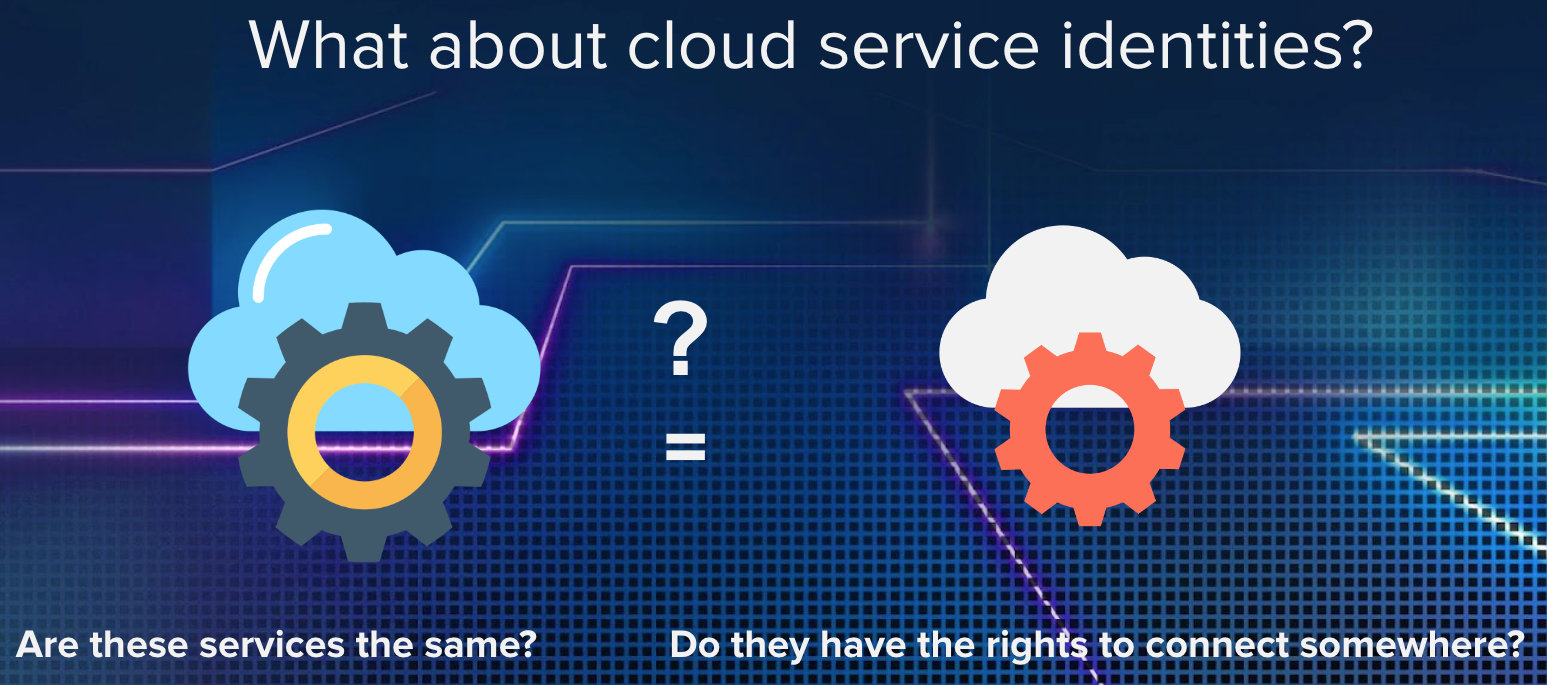
In the legacy world we would segregate the network, use vlan or mac address, but in the cloud? Cloud Workloads or VMs can be upgraded or reinstalled in seconds, and born again with different characteristics, so how can we recognize them?
CyberArk Conjur is the answer!
Let's start from the beginning: Conjur is a secrets manager, and its logic is represented below
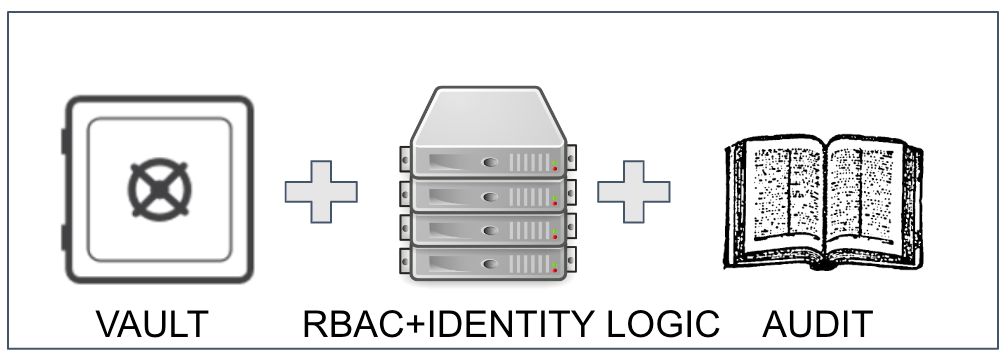
The secrets are stored in Conjur as text, and in the IT this means
- Privileged account credentials
- Passwords
- Certificates
- SSH keys
- API keys
- Encryption keys
Conjur is doing the magic serving the secrets through the authenticators, and dedicated plugins used to perform secure and native integrations. Below you can see the complete list of the authenticators currently available:
To understand how authenticators work, let's see a couple of examples.
Below is how an application authenticates itself with Conjur, using a JWT token to establish a secure connection, and obtain the secrets.
Another great example of integration is the Kubernetes integration. Differently from JWT, here we have a dedicated component, Conjur Follower, that is installed on Kubernetes and acts as a local secret-proxy cache.
The Conjur Follower can guarantee an additional level of fault tolerance, it serves the secrets locally without network latency, and it does it in the most secure way using a mTLS connection!
Now that we have seen how Conjur can connect and serve applications, let's consider what it can serve:

If you need another reason to adopt Conjur, think about a multi-cloud environment. Conjur acts as a single point of truth for secrets, security policies and audits. Security islands are avoided! While every cloud provider handles secrets differently, with Conjur you decide your security level, and you apply it in the same way to every service.
CyberArk Conjur enterprise is great, but products without expertise are not the solution! SIGHUP is here to HELP!
We have already deployed it in several environments, and we know how to:
- draw the best product architecture
- structure the policy repository
- build the integrations
If you are interested in CyberArk Conjur, feel free to reach me on Twitter for further details or contact the SIGHUP sales team.
