Snyk and Shift-Left approach: Boosting your security compliance with ease.
This article will provide a brief overview, some example use cases on Snyk's tools and features, and how we used it to improve Kubernetes Fury Distribution's security.

As you may have already read in our recent article, we announced our Partnership with Snyk. Still, already from some months, our DevSecOps Team had been studying, testing, and experimenting with Snyk tools to confidently add them to our "Security toolset". This article will provide a brief overview, some example use cases on Snyk's tools and features, and how we used it to improve Kubernetes Fury Distribution's security.
What is Snyk? Snyk is a security platform that allows developers to scan their code for vulnerabilities and security issues, and provides fixes and recommendations for how to remediate them.
Some key features of Snyk include:
• Dependency scanning: Snyk can automatically scan your application's dependencies to identify known vulnerabilities. This allows you to find and fix vulnerabilities early in the development process before they make it into production.
• Continuous integration and delivery (CI/CD) integration: Snyk integrates seamlessly with popular CI/CD tools like Jenkins, CircleCI, and Travis CI, allowing you to automatically scan your dependencies at every stage of the development process.
• Fix suggestions: When Snyk identifies a vulnerability in your dependencies, it will provide you with a fix suggestion that you can use to quickly and easily fix the vulnerability.
• Security policies: Snyk allows you to set up custom security policies that define what level of risk is acceptable for your application. If a vulnerability is found that exceeds your defined level of risk, Snyk will alert you so that you can take action to fix it.
• Third-party library analysis: Snyk can help you understand the security risk of using third-party libraries in your application. It will provide you with information about the known vulnerabilities in these libraries, allowing you to make informed decisions about which libraries to use.
What is a Shift-Left approach?
It's a practice in the DevSecOps methodology that aims to move security measures and testing earlier in the software development process. Shift-left aims to identify and address potential security vulnerabilities as early as possible in the development cycle, rather than waiting until later stages or even after the software has been deployed.
That also helps to improve the overall quality of the software being developed, as it encourages developers to consider and integrate security measures into their code from the beginning. This can lead to more robust and secure software.
How we made use of Snyk to improve Fury Kubernetes Distribution security
We first imported the repository into Snyk Dashboard, then a scan is performed to check all the major vulnerabilities. For this example, we used our Gatekeeper module (https://github.com/sighupio/gatekeeper-policy-manager).
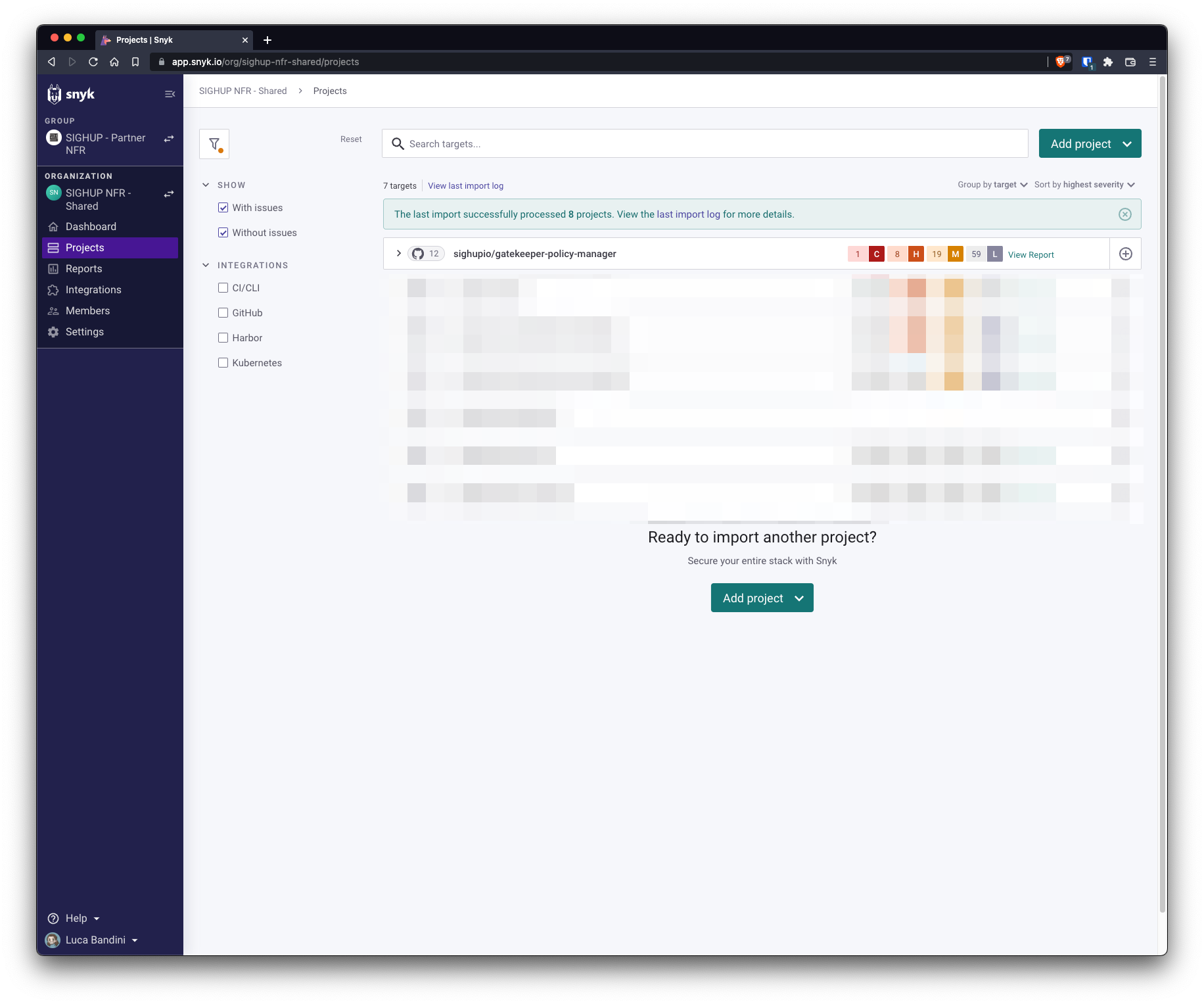
After some time scanning, Snyk will prompt us with a summary of the found vulnerabilities. Indeed, as a static analysis, at this step is not certain that the found vulnerabilities are in fact impacting the product. You can see the number and the severity level together with the responsible file.
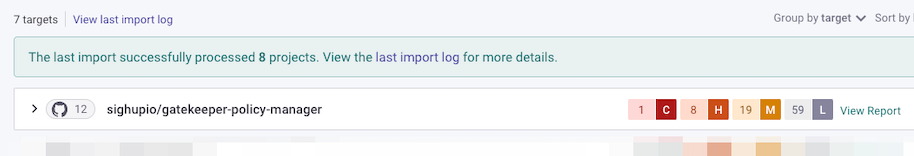
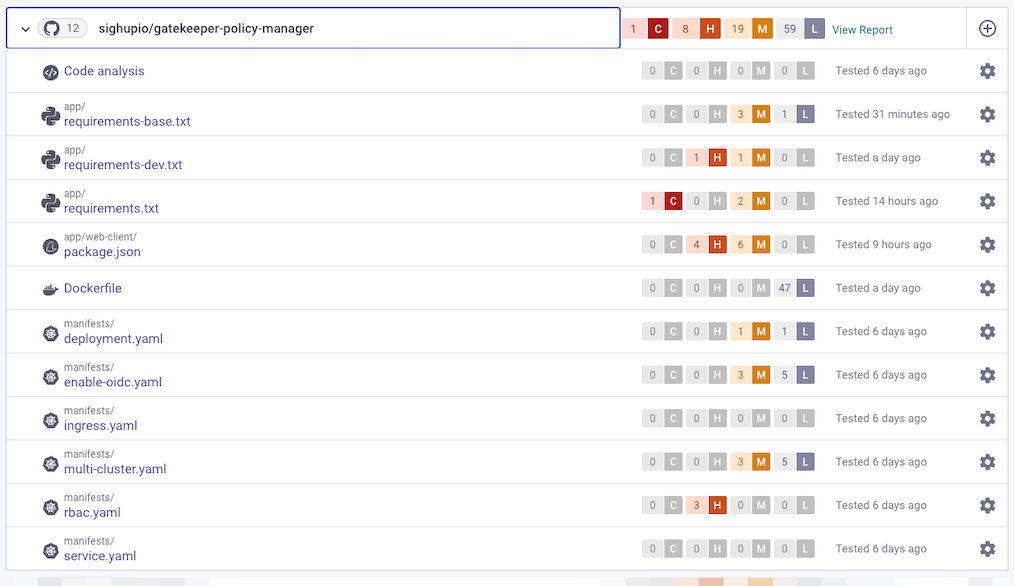
We will take one High severity vulnerability as an example. Expanding it we can see more details about it in a really clear way, together with a priority score, remediation methods, and even a link to a learning page talking about it.
If we click on "Fix this vulnerability" we automatically open a PR to the project clearly stating all the information about it, easily comprehensible by the developer who will review it and hopefully merge it.
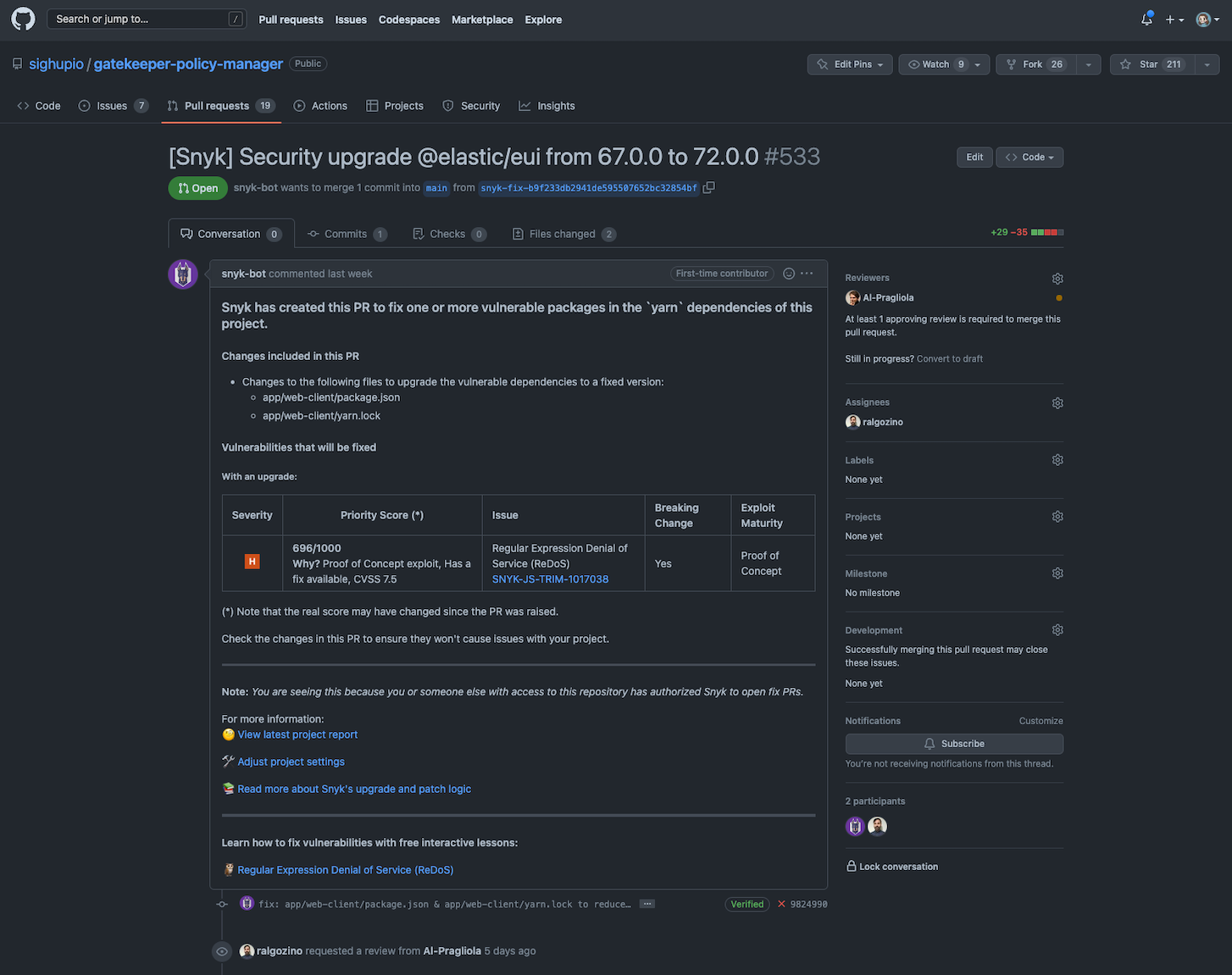
This is really a great feature because it creates awareness among the developers on security vulnerabilities that would be otherwise not taken into consideration or not given adequate priority.
Conclusions
That's the idea behind a shift-left approach, moving the security checks back to the code developer level, without slowing down their work or putting roadblocks.

